DDoS attacks represent one of the most prevalent and damaging cybersecurity threats facing websites and online services today.
Understanding DDoS Attacks: A Serious Threat to Online Security
DDoS attacks represent one of the most prevalent and damaging cybersecurity threats facing websites and online services today. Despite their widespread impact, many website owners don't fully understand how these attacks work or why protecting against them is critical for both SEO performance and user engagement.
What Exactly is a DDoS Attack?
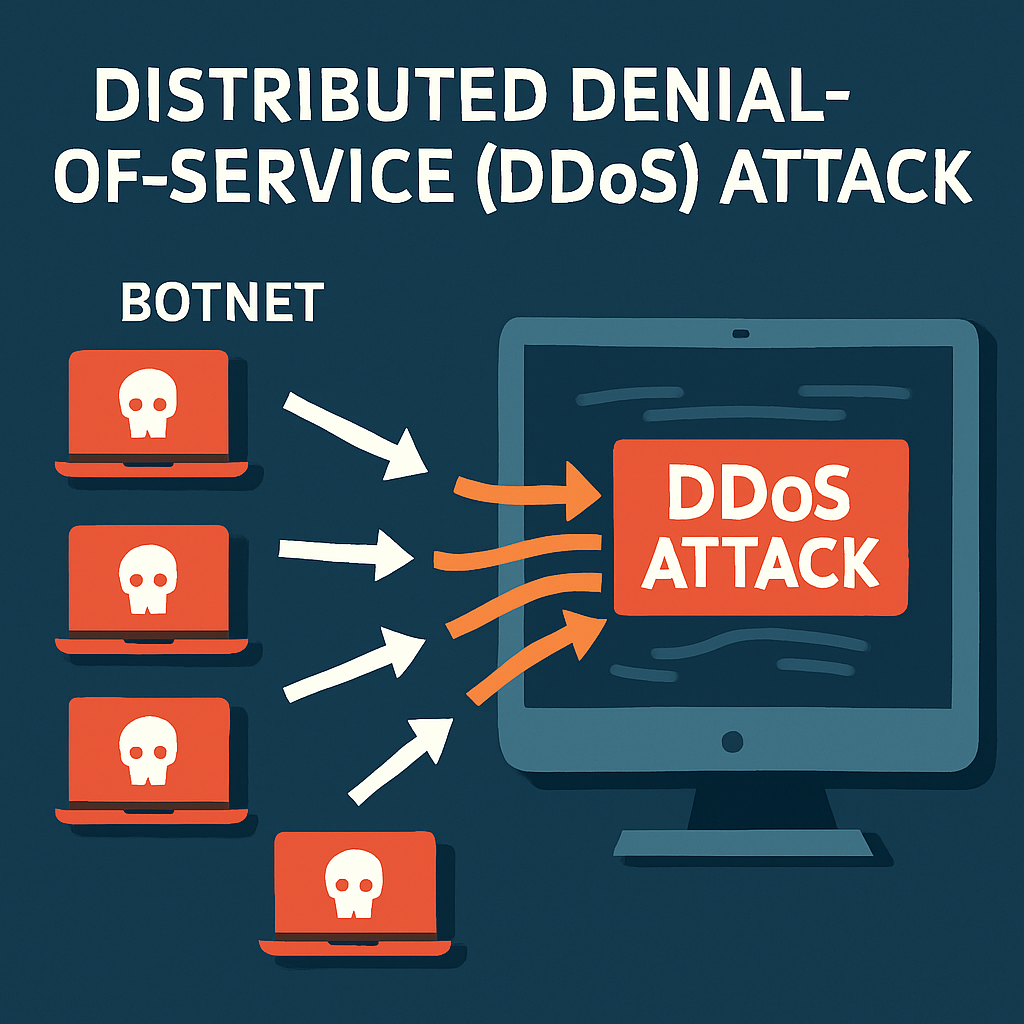
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to disrupt a website or online service by overwhelming it with a flood of internet traffic from multiple sources. Unlike regular traffic patterns, this coordinated assault aims to render the target inaccessible to legitimate users.
Think of it as a massive traffic jam deliberately created to prevent normal visitors from reaching their destination. When successful, these attacks can take down websites, applications, or entire networks.
How DDoS Attacks Work
DDoS attacks achieve their disruptive power by utilizing networks of compromised devices-often called botnets. These networks consist of ordinary computers and IoT devices infected with malware that allows attackers to control them remotely.
During an attack, the attacker instructs these "zombie" devices to simultaneously send requests to the target's server or network. Because the traffic comes from many different sources, it's particularly difficult to block. The targeted system becomes overwhelmed trying to process all these requests, eventually slowing down or crashing completely.
Types of DDoS Attacks
DDoS attacks come in several varieties, each targeting different vulnerabilities:
Application Layer Attacks (Layer 7)
These sophisticated attacks target the "top" layer in the networking model where web applications operate. They focus on exhausting server resources by overwhelming them with seemingly legitimate requests like HTTP GET and POST. What makes these attacks particularly dangerous is that they require less bandwidth to cause significant disruption.
Network Layer Attacks (Layer 3)
Layer 3 attacks target the network infrastructure itself, attempting to consume all available bandwidth or overwhelm network equipment. These attacks often use protocols like ICMP to flood the target's network capacity.
Volumetric Attacks
The most common form of DDoS, volumetric attacks simply aim to consume all available bandwidth between the victim and the internet by generating massive traffic volumes.
The Real Cost of DDoS Attacks
The financial impact of DDoS attacks is staggering. According to recent data, the average DDoS attack costs businesses approximately $6,000 per minute. With the average attack lasting 68 minutes in 2023, that translates to over $400,000 per incident.
Even more concerning, the duration of attacks surged by more than 400% from Q1 to Q4 of 2023-from an average of 24 minutes to 121 minutes.
But the true cost extends beyond immediate financial losses:
Brand Reputation Damage
DDoS attacks severely damage a company's reputation and erode customer trust. Customers experiencing service disruptions may perceive the company as unreliable or insecure.
Long-term Revenue Loss
The negative impact on customer loyalty and acquisition often continues long after the attack has ended.
Recent DDoS Attack Trends
The threat landscape is evolving rapidly:
A 53% increase in DDoS attacks was recorded in 2024 compared to the previous year
Cloudflare alone blocked approximately 21.3 million DDoS attacks over a 12-month period
A dramatic 1,885% surge in attacks exceeding 1 Tbps occurred between Q3 and Q4 of 2024
The largest attack ever recorded reached 5.6 terabits per second, targeting an ISP in Eastern Asia
Effective DDoS Mitigation Strategies
Protecting against DDoS attacks requires a multi-layered approach:
Traffic Analysis and Filtering
Effective DDoS mitigation begins with identifying baseline conditions for normal network traffic and analyzing patterns to detect anomalies. Advanced systems can separate legitimate human traffic from bot traffic by examining various attributes like IP addresses, cookie variations, and HTTP headers.
Cloud-Based Protection
Using content delivery networks (CDNs) and specialized DDoS protection services can help absorb and filter malicious traffic before it reaches your servers.
Advanced Detection Technologies
Modern detection methods employ machine learning algorithms to identify attack patterns and adjust security thresholds dynamically.
Why DDoS Protection Matters for Your Website
Protecting your website against DDoS attacks isn't just about security-it directly impacts:
SEO Performance
Search engines prioritize website availability and speed. When your site experiences downtime due to DDoS attacks, search rankings can decline significantly.
User Experience
Even minor performance degradation can dramatically affect user satisfaction and conversion rates.
Business Continuity
For online businesses, website availability directly correlates with revenue generation.
Conclusion
As DDoS attacks continue to grow in frequency, size, and sophistication, implementing robust protection measures isn't optional-it's essential for maintaining online presence and business continuity. Whether you're running a small business website or managing enterprise-level applications, understanding and mitigating DDoS threats should be a core component of your cybersecurity strategy.
Ready to check if your website is properly protected? Try Kodx.uk's free redirect checker to identify potential vulnerabilities in your URL structure and ensure your site remains secure and accessible even under attack conditions.
DDoS attacks represent one of the most prevalent and damaging cybersecurity threats facing websites and online services today. Despite their widespread impact, many website owners don't fully understand how these attacks work or why protecting against them is critical for both SEO performance and user engagement.
What Exactly is a DDoS Attack?
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to disrupt a website or online service by overwhelming it with a flood of internet traffic from multiple sources. Unlike regular traffic patterns, this coordinated assault aims to render the target inaccessible to legitimate users.
Think of it as a massive traffic jam deliberately created to prevent normal visitors from reaching their destination. When successful, these attacks can take down websites, applications, or entire networks.
How DDoS Attacks Work
DDoS attacks achieve their disruptive power by utilizing networks of compromised devices-often called botnets. These networks consist of ordinary computers and IoT devices infected with malware that allows attackers to control them remotely.
During an attack, the attacker instructs these "zombie" devices to simultaneously send requests to the target's server or network. Because the traffic comes from many different sources, it's particularly difficult to block. The targeted system becomes overwhelmed trying to process all these requests, eventually slowing down or crashing completely.
Types of DDoS Attacks
DDoS attacks come in several varieties, each targeting different vulnerabilities:
Application Layer Attacks (Layer 7)
These sophisticated attacks target the "top" layer in the networking model where web applications operate. They focus on exhausting server resources by overwhelming them with seemingly legitimate requests like HTTP GET and POST. What makes these attacks particularly dangerous is that they require less bandwidth to cause significant disruption.
Network Layer Attacks (Layer 3)
Layer 3 attacks target the network infrastructure itself, attempting to consume all available bandwidth or overwhelm network equipment. These attacks often use protocols like ICMP to flood the target's network capacity.
Volumetric Attacks
The most common form of DDoS, volumetric attacks simply aim to consume all available bandwidth between the victim and the internet by generating massive traffic volumes.
The Real Cost of DDoS Attacks
The financial impact of DDoS attacks is staggering. According to recent data, the average DDoS attack costs businesses approximately $6,000 per minute. With the average attack lasting 68 minutes in 2023, that translates to over $400,000 per incident.
Even more concerning, the duration of attacks surged by more than 400% from Q1 to Q4 of 2023-from an average of 24 minutes to 121 minutes.
But the true cost extends beyond immediate financial losses:
Brand Reputation Damage
DDoS attacks severely damage a company's reputation and erode customer trust. Customers experiencing service disruptions may perceive the company as unreliable or insecure.
Long-term Revenue Loss
The negative impact on customer loyalty and acquisition often continues long after the attack has ended.
Recent DDoS Attack Trends
The threat landscape is evolving rapidly:
A 53% increase in DDoS attacks was recorded in 2024 compared to the previous year
Cloudflare alone blocked approximately 21.3 million DDoS attacks over a 12-month period
A dramatic 1,885% surge in attacks exceeding 1 Tbps occurred between Q3 and Q4 of 2024
The largest attack ever recorded reached 5.6 terabits per second, targeting an ISP in Eastern Asia
Effective DDoS Mitigation Strategies
Protecting against DDoS attacks requires a multi-layered approach:
Traffic Analysis and Filtering
Effective DDoS mitigation begins with identifying baseline conditions for normal network traffic and analyzing patterns to detect anomalies. Advanced systems can separate legitimate human traffic from bot traffic by examining various attributes like IP addresses, cookie variations, and HTTP headers.
Cloud-Based Protection
Using content delivery networks (CDNs) and specialized DDoS protection services can help absorb and filter malicious traffic before it reaches your servers.
Advanced Detection Technologies
Modern detection methods employ machine learning algorithms to identify attack patterns and adjust security thresholds dynamically.
Why DDoS Protection Matters for Your Website
Protecting your website against DDoS attacks isn't just about security-it directly impacts:
SEO Performance
Search engines prioritize website availability and speed. When your site experiences downtime due to DDoS attacks, search rankings can decline significantly.
User Experience
Even minor performance degradation can dramatically affect user satisfaction and conversion rates.
Business Continuity
For online businesses, website availability directly correlates with revenue generation.
Conclusion
As DDoS attacks continue to grow in frequency, size, and sophistication, implementing robust protection measures isn't optional-it's essential for maintaining online presence and business continuity. Whether you're running a small business website or managing enterprise-level applications, understanding and mitigating DDoS threats should be a core component of your cybersecurity strategy.
Ready to check if your website is properly protected? Try Kodx.uk's free redirect checker to identify potential vulnerabilities in your URL structure and ensure your site remains secure and accessible even under attack conditions.